my Linux stuff
Some tricks and stuff I collected around Linux Virtualization Cloud and NFV
Friday, April 24, 2020
Sunday, September 2, 2018
How to circumvent Netflix VPN detection
Netflix is a great service, cool content, good quality and its available from anywhere.
The not so cool feature I found out they had is limiting content to geographical locations.
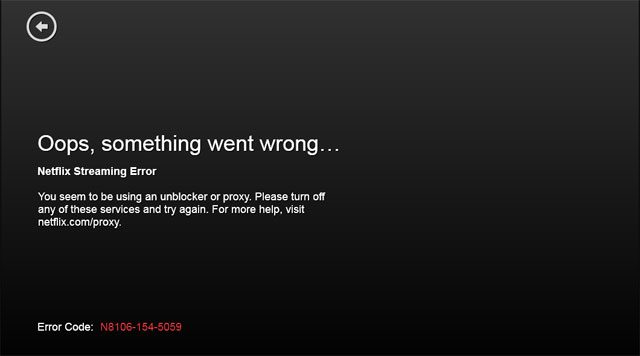
I was in Israel and read an article listing the best movies of 2018 in Netflix, that night I tried to search in my Netflix for some of the movies and came up short, as if the movies where never on Netflix, I thought they might playing me so I used Hola plugin in my chrome to get to Netflix US, when I searched the Netflix site coming from the US I could suddenly find all the movies that were unavailable coming from Israel, but when I tried to watch them I got an error message that Netflix detected that I'm using a proxy or a VPN and will not allow me to watch the movie this way.
So here my quest to find a free VPN service begins, I downloaded dozens of VPN open source ones like UltraSurf Freemium ones and basically most of those that are out there. but Netflix kept identifying those VPNs. The only one that did work was TunnelBear which gives you 500MB for free, so I watched half of the movie and then the 500MB were out and I continued my search for a working free VPN, after 2-3 hours of installing VPNs and testing them I gave up and decided to Hack it. I went to my AWS account and created the free tier VM and a key-pair to access it and downloaded the PEM file, then got the SSH command in the AWS access screen:
I used the example to connect via SSH to the VM but Ive added an additional parameter that will change the game.
first you need to download the .pem key file from AWS and change its security privileges this way:
sudo chmod 400 pair.pem
Then just SSH with the following command to the address you got from AWS:
sudo ssh -D 9999 -i "pair.pem" ubuntu@[address of your VM in AWS]
The "-D 9999" is the part that says it will forward all traffic via that port.
now open your favorite browser and configure it to connect to port 9999 as follow(I used Mozilla):
example with mac+chrome:
Now open a new tab on the browser and go to Netflix and your routed from the AWS region your VM is running in
ENjoy!!
first you need to download the .pem key file from AWS and change its security privileges this way:
sudo chmod 400 pair.pem
Then just SSH with the following command to the address you got from AWS:
sudo ssh -D 9999 -i "pair.pem" ubuntu@[address of your VM in AWS]
The "-D 9999" is the part that says it will forward all traffic via that port.
now open your favorite browser and configure it to connect to port 9999 as follow(I used Mozilla):
Now open a new tab on the browser and go to Netflix and your routed from the AWS region your VM is running in
ENjoy!!
Sunday, July 12, 2015
Speed test from CMD
# wget -O speedtest-cli https://raw.github.com/sivel/speedtest-cli/master/speedtest_cli.py
# chmod +x speedtest-cli
# ./speedtest-cli
if pip does not work but is installed like here:
root@ubuntu12:~# pip -v
-bash: /usr/bin/pip: No such file or directory
root@ubuntu12:~# which pip
/usr/local/bin/pip
root@ubuntu12:~# pip
-bash: /usr/bin/pip: No such file or directory
root@ubuntu12:~# type pip
pip is hashed (/usr/bin/pip)
Just run: # hash -r
root@ubuntu12:~# hash -r
root@ubuntu12:~# pip
Usage:
pip <command> [options]
Commands:
install Install packages.
uninstall Uninstall packages.
freeze Output installed packages in requirements format.
list List installed packages.
show Show information about installed packages.
search Search PyPI for packages.
wheel Build wheels from your requirements.
help Show help for commands.
General Options:
-h, --help Show help.
--isolated Run pip in an isolated mode, ignoring environment variables and user configuration.
-v, --verbose Give more output. Option is additive, and can be used up to 3 times.
-V, --version Show version and exit.
-q, --quiet Give less output.
--log <path> Path to a verbose appending log.
--proxy <proxy> Specify a proxy in the form [user:passwd@]proxy.server:port.
--retries <retries> Maximum number of retries each connection should attempt (default 5 times).
--timeout <sec> Set the socket timeout (default 15 seconds).
--exists-action <action> Default action when a path already exists: (s)witch, (i)gnore, (w)ipe, (b)ackup.
--trusted-host <hostname> Mark this host as trusted, even though it does not have valid or any HTTPS.
--cert <path> Path to alternate CA bundle.
--client-cert <path> Path to SSL client certificate, a single file containing the private key and the certificate in PEM format.
--cache-dir <dir> Store the cache data in <dir>.
--no-cache-dir Disable the cache.
--disable-pip-version-check
Don't periodically check PyPI to determine whether a new version of pip is available for download. Implied with --no-index.
root@ubuntu12:~#
Tuesday, July 7, 2015
Install & configure OpenVPN
#files:
lzo-2.06-1.el6.rfx.x86_64.rpm (http://pkgs.repoforge.org/lzo/lzo-2.06-1.el6.rfx.x86_64.rpm)
pkcs11-helper-1.10.tar.bz2 ()
if you are running on centos5 try this file: http://pkgs.repoforge.org/lzo/lzo-minilzo-2.06-1.el5.rf.x86_64.rpm
#dependencies:
#run:
rpm -ivh /tmp/lzo-2.06-1.el6.rfx.x86_64.rpm
#run
rpmbuild -tb /tmp/pkcs11-helper-1.10.tar.bz2
#run:(if this doesnt work search for pkcs11-helper like this: find / -name 'pkcs11-helper*' )
rpm -ivh /root/rpmbuild/RPMS/x86_64/pkcs11-helper-1.10-2.x86_64.rpm /root/rpmbuild/RPMS/x86_64/pkcs11-helper-devel-1.10-2.x86_64.rpm
#run:
rpm -ivh /tmp/openvpn-2.1.4-2.el6.rf.x86_64.rpm
Configuring openvpn
# cd /usr/share/doc/openvpn-2.0.9
# cp -av easy-rsa /etc/openvpn/
# cd /etc/openvpn/easy-rsa/
# vim vars
In the vars file, edit the KEY_* entries at the bottom of the file, such as KEY_COUNTRY, KEY_ORG, KEY_EMAIL, etc. These will be used to build the OpenSSL certificates. Next, it’s time to initialize the PKI:
# . ./vars
# sh clean-all
# sh build-ca
# sh build-key-server server
For the above, and the below client certificates, you can enter pretty much anything for the “Common Name” field, however there is a certain logic to use: “OpenVPN-CA” when generating the Certificate Authority, “server” when generating the server certificate, and “client” or the name of the specific client system for the client certificates. Those certificates are generated with:
# sh build-key client1
# sh build-key client2
The next step is to generate the Diffie Hellman parameters for the server:
# sh build-dh
When this is done, you will have a number of files in the keys/ subdirectory. At this point, for the clients, you want to copy the appropriate files to them securely (i.e., via SSH or on a USB stick); the files the clients need are ca.crt, client1.crt, and client1.key (or whatever you named the files when you generated them with the build-key script).
Next, create the OpenVPN server configuration file. To get up and running quickly, copy one of the example config files:
# cd /etc/openvpn/
# cp /usr/share/doc/openvpn-2.1.4/sample-config-files/server.conf .
# vim server.conf
The aim here is to get this going right away, so we won’t examine each of the options in detail. The primary things you want to do are to uncomment the “user” and “group” directives, to make the openvpn process run as the unprivileged “nobody” user. You may also want to change the “local” directive to make it listen to one specific IP address. This would be the IP to which your firewall is forwarding UDP port 1194. As well, you will want to set the “client-to-client” directive to enable it, and also set the “push” directives for route and DNS options. What follows is a comment-stripped server.conf, as an example:
local 192.168.10.11
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh1024.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "route 192.168.10.0 255.255.254.0"
push "dhcp-option DNS 192.168.10.12"
push "dhcp-option DOMAIN domain.com"
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
Finally, copy the required keys and certificates that you previously generated:
# cd /etc/openvpn/
# cp easy-rsa/keys/ca.crt .
# cp easy-rsa/keys/server.{key,crt} .
# cp easy-rsa/keys/dh1024.pem .
And, finally, start the OpenVPN server:
# /etc/init.d/openvpn start
To get routing set up properly on the server so that remote clients, when they connect, can reach more than just the server itself, you will need to enable IP forwarding. This can be done by the following:
# echo 1 > /proc/sys/net/ipv4/ip_forward
You can also do it by editing /etc/sysctl.conf and adding the following (this is a good thing to do as it will ensure that packet-forwarding persists across reboots):
net.ipv4.ip_forward = 1
You also want to ensure that packets going back to the client system are routed properly. This can be done by changing the route on the gateway of the server’s network to route packets to the client network (10.8.0.1/32) through the OpenVPN server (if the server happens to be the gateway as well, you don’t have to do anything additional to accomplish this). How this is done largely depends on the operating system of the gateway.
Once this is done, you should be able to ping any machine on the server’s LAN from the client, and be able to ping the client from any machine on the server’s LAN. For instance, from a machine on the server LAN (not the server):
% traceroute 10.8.0.6
traceroute to 10.8.0.6 (10.8.0.6), 64 hops max, 52 byte packets
1 fw (192.168.10.1) 0.848 ms 0.342 ms 0.249 ms
2 server (192.168.10.11) 0.214 ms 0.231 ms 0.243 ms
3 server (192.168.10.11) 0.199 ms !Z 0.443 ms !Z 0.396 ms !Z
% ping 10.8.0.6
PING 10.8.0.6 (10.8.0.6): 56 data bytes
64 bytes from 10.8.0.6: icmp_seq=0 ttl=63 time=17.540 ms
And from the client:
# traceroute 192.168.10.65
traceroute to 192.168.10.65 (192.168.10.65), 30 hops max, 40 byte packets
1 10.8.0.1 (10.8.0.1) 22.963 ms 27.311 ms 27.317 ms
2 10.8.0.1 (10.8.0.1) 27.297 ms !X 27.294 ms !X 27.269 ms !X
# ping 192.168.10.65
PING 192.168.10.65 (192.168.10.65) 56(84) bytes of data.
64 bytes from 192.168.10.65: icmp_seq=1 ttl=62 time=515 ms
The setting up of OpenVPN clients will be the subject of two tips in the next week. I’ve made the assumption that the client is correctly configured here, simply to illustrate how it should look when it all works together, but in the next parts of this series we will get into more depth with the client configuration.
Download the PDF, “How to set up OpenVPN server and create Linux and Mac OS X clients.“
Get IT Tips, news, and reviews delivered directly to your inbox by subscribing to TechRepublic’s free newsletters.
lzo-2.06-1.el6.rfx.x86_64.rpm (http://pkgs.repoforge.org/lzo/lzo-2.06-1.el6.rfx.x86_64.rpm)
pkcs11-helper-1.10.tar.bz2 ()
if you are running on centos5 try this file: http://pkgs.repoforge.org/lzo/lzo-minilzo-2.06-1.el5.rf.x86_64.rpm
#dependencies:
#run:
rpm -ivh /tmp/lzo-2.06-1.el6.rfx.x86_64.rpm
#run
rpmbuild -tb /tmp/pkcs11-helper-1.10.tar.bz2
#run:(if this doesnt work search for pkcs11-helper like this: find / -name 'pkcs11-helper*' )
rpm -ivh /root/rpmbuild/RPMS/x86_64/pkcs11-helper-1.10-2.x86_64.rpm /root/rpmbuild/RPMS/x86_64/pkcs11-helper-devel-1.10-2.x86_64.rpm
#run:
rpm -ivh /tmp/openvpn-2.1.4-2.el6.rf.x86_64.rpm
Configuring openvpn
# cd /usr/share/doc/openvpn-2.0.9
# cp -av easy-rsa /etc/openvpn/
# cd /etc/openvpn/easy-rsa/
# vim vars
In the vars file, edit the KEY_* entries at the bottom of the file, such as KEY_COUNTRY, KEY_ORG, KEY_EMAIL, etc. These will be used to build the OpenSSL certificates. Next, it’s time to initialize the PKI:
# . ./vars
# sh clean-all
# sh build-ca
# sh build-key-server server
For the above, and the below client certificates, you can enter pretty much anything for the “Common Name” field, however there is a certain logic to use: “OpenVPN-CA” when generating the Certificate Authority, “server” when generating the server certificate, and “client” or the name of the specific client system for the client certificates. Those certificates are generated with:
# sh build-key client1
# sh build-key client2
The next step is to generate the Diffie Hellman parameters for the server:
# sh build-dh
When this is done, you will have a number of files in the keys/ subdirectory. At this point, for the clients, you want to copy the appropriate files to them securely (i.e., via SSH or on a USB stick); the files the clients need are ca.crt, client1.crt, and client1.key (or whatever you named the files when you generated them with the build-key script).
Next, create the OpenVPN server configuration file. To get up and running quickly, copy one of the example config files:
# cd /etc/openvpn/
# cp /usr/share/doc/openvpn-2.1.4/sample-config-files/server.conf .
# vim server.conf
The aim here is to get this going right away, so we won’t examine each of the options in detail. The primary things you want to do are to uncomment the “user” and “group” directives, to make the openvpn process run as the unprivileged “nobody” user. You may also want to change the “local” directive to make it listen to one specific IP address. This would be the IP to which your firewall is forwarding UDP port 1194. As well, you will want to set the “client-to-client” directive to enable it, and also set the “push” directives for route and DNS options. What follows is a comment-stripped server.conf, as an example:
local 192.168.10.11
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key # This file should be kept secret
dh dh1024.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "route 192.168.10.0 255.255.254.0"
push "dhcp-option DNS 192.168.10.12"
push "dhcp-option DOMAIN domain.com"
client-to-client
keepalive 10 120
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
Finally, copy the required keys and certificates that you previously generated:
# cd /etc/openvpn/
# cp easy-rsa/keys/ca.crt .
# cp easy-rsa/keys/server.{key,crt} .
# cp easy-rsa/keys/dh1024.pem .
And, finally, start the OpenVPN server:
# /etc/init.d/openvpn start
To get routing set up properly on the server so that remote clients, when they connect, can reach more than just the server itself, you will need to enable IP forwarding. This can be done by the following:
# echo 1 > /proc/sys/net/ipv4/ip_forward
You can also do it by editing /etc/sysctl.conf and adding the following (this is a good thing to do as it will ensure that packet-forwarding persists across reboots):
net.ipv4.ip_forward = 1
You also want to ensure that packets going back to the client system are routed properly. This can be done by changing the route on the gateway of the server’s network to route packets to the client network (10.8.0.1/32) through the OpenVPN server (if the server happens to be the gateway as well, you don’t have to do anything additional to accomplish this). How this is done largely depends on the operating system of the gateway.
Once this is done, you should be able to ping any machine on the server’s LAN from the client, and be able to ping the client from any machine on the server’s LAN. For instance, from a machine on the server LAN (not the server):
% traceroute 10.8.0.6
traceroute to 10.8.0.6 (10.8.0.6), 64 hops max, 52 byte packets
1 fw (192.168.10.1) 0.848 ms 0.342 ms 0.249 ms
2 server (192.168.10.11) 0.214 ms 0.231 ms 0.243 ms
3 server (192.168.10.11) 0.199 ms !Z 0.443 ms !Z 0.396 ms !Z
% ping 10.8.0.6
PING 10.8.0.6 (10.8.0.6): 56 data bytes
64 bytes from 10.8.0.6: icmp_seq=0 ttl=63 time=17.540 ms
And from the client:
# traceroute 192.168.10.65
traceroute to 192.168.10.65 (192.168.10.65), 30 hops max, 40 byte packets
1 10.8.0.1 (10.8.0.1) 22.963 ms 27.311 ms 27.317 ms
2 10.8.0.1 (10.8.0.1) 27.297 ms !X 27.294 ms !X 27.269 ms !X
# ping 192.168.10.65
PING 192.168.10.65 (192.168.10.65) 56(84) bytes of data.
64 bytes from 192.168.10.65: icmp_seq=1 ttl=62 time=515 ms
The setting up of OpenVPN clients will be the subject of two tips in the next week. I’ve made the assumption that the client is correctly configured here, simply to illustrate how it should look when it all works together, but in the next parts of this series we will get into more depth with the client configuration.
Download the PDF, “How to set up OpenVPN server and create Linux and Mac OS X clients.“
Get IT Tips, news, and reviews delivered directly to your inbox by subscribing to TechRepublic’s free newsletters.
Thursday, April 16, 2015
Install Ansible : Great tool for cluster mgmt http://docs.ansible.com/intro_installation.html note:make sure that all of your hosts are ssh via key Install on Centos: #sudo yum install ansible go to the /etc/ansible/hosts and edit it like the following example: # This is the default ansible 'hosts' file. # # It should live in /etc/ansible/hosts # # - Comments begin with the '#' character # - Blank lines are ignored # - Groups of hosts are delimited by [header] elements # - You can enter hostnames or ip addresses # - A hostname/ip can be a member of multiple groups # Ex 1: Ungrouped hosts, specify before any group headers. #green.example.com 10.20.0.2 [servers] 10.20.0.3 10.20.0.4 10.20.0.5 10.20.0.6 10.20.0.7 10.20.0.8 [computes] 10.20.0.4 10.20.0.5 10.20.0.6 10.20.0.7 10.20.0.8 [mesos] 111.111.111.15 111.111.111.16 Now to run a command: example #1 run cmd on all servers #ansible all -a "date" 10.20.0.4 | success | rc=0 >> Thu Apr 16 10:18:27 UTC 2015 10.20.0.6 | success | rc=0 >> Thu Apr 16 10:18:27 UTC 2015 10.20.0.7 | success | rc=0 >> Thu Apr 16 10:18:27 UTC 2015 10.20.0.5 | success | rc=0 >> Thu Apr 16 10:18:27 UTC 2015 10.20.0.8 | success | rc=0 >> Thu Apr 16 10:18:28 UTC 2015 10.20.0.2 | success | rc=0 >> Thu Apr 16 10:18:28 UTC 2015 111.111.111.16 | success | rc=0 >> Thu Apr 16 10:18:28 UTC 2015 111.111.111.15 | success | rc=0 >> Thu Apr 16 10:18:28 UTC 2015 10.20.0.3 | success | rc=0 >> Thu Apr 16 10:18:28 UTC 2015 example #2 run hostname cmd on all servers # ansible computes -a "hostname" 10.20.0.8 | success | rc=0 >> node-6.domain.tld 10.20.0.4 | success | rc=0 >> node-2.domain.tld 10.20.0.6 | success | rc=0 >> node-4.domain.tld 10.20.0.7 | success | rc=0 >> node-5.domain.tld 10.20.0.5 | success | rc=0 >> node-3.domain.tld
Sunday, March 15, 2015
example for iptables on centos:
# configuration written by system-config-securitylevel
# Manual customization of this file is not recommended.
#################################################################################
# Filtering table:
#################################################################################
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
######################################################
# INPUT - beginning
# -----------------
# allow packets of already established connections:
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
# INPUT to firewall from loopback - all allowed (lo)
# --------------------------------------------------
-A INPUT -i lo -j ACCEPT
# INPUT to firewall - from NTTNode (eth2)
# --------------------------------------
# allow any traffic from inside:
-A INPUT -i eth2 -j ACCEPT
# INPUT to firewall - from OpenVPN connections (tun0)
# ---------------------------------------------------
# allow any traffic for OpenVPN clients:
-A INPUT -i tun0 -s 192.168.100.0/24 -j ACCEPT
# INPUT to firewall - from KVM VMs connections (virbr0)
# ---------------------------------------------------
# allow any traffic for KVM VMs:
-A INPUT -i virbr0 -s 10.80.90.0/24 -j ACCEPT
# INPUT to firewall - from Internet (eth3)
# ----------------------------------------
# allow pings for connection testing:
-A INPUT -i eth0 -p icmp --icmp-type echo-request -j ACCEPT
#
# allow incoming OpenVPN connections:
-A INPUT -i eth0 -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT
-A INPUT -i eth0 -p udp -m state --state NEW -m udp --dport 1194 -j ACCEPT
#
# allow SSH on port 22000
-A INPUT -i eth0 -p tcp -m tcp --dport 22000 -m state --state NEW -j ACCEPT
######################################################
# FORWARDING - beginning
# ----------------------
# allow packets of already established connections:
-A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
# FORWARDING - from NTTNode to Internet (eth2 --> eth0)
# ----------------------------------------------------
# allow any outgoing traffic:
-A FORWARD -i eth2 -o eth0 -j ACCEPT
# FORWARDING - from NTTNode to OpenVPN clients (eth0 --> tun0)
# -----------------------------------------------------------
# FORWARDING - from Internet to CI VM (eth0 --> virbr0)
# ---------------------------------------------------
-A FORWARD -i eth0 -o virbr0 -j ACCEPT
# FORWARDING - from NTTNode to CI VM (eth2 --> virbr0)
# ---------------------------------------------------
-A FORWARD -i eth2 -o virbr0 -j ACCEPT
# FORWARDING - from OpenVPN to Node12 (tun0 --> eth2)
# ---------------------------------------------------
# allow any traffic for OpenVPN users:
-A FORWARD -i tun0 -o eth2 -s 192.168.100.0/24 -j ACCEPT
# FORWARDING - from CI VM to NTTNode (virbr0 --> eth2)
# ----------------------------------------------------
# allow any traffic for OpenVPN users:
-A FORWARD -i virbr0 -o eth2 -j ACCEPT
# FORWARDING - from CI VM to Internet (virbr0 --> eth0)
# ----------------------------------------------------
# allow any traffic for OpenVPN users:
-A FORWARD -i virbr0 -o eth0 -j ACCEPT
# FORWARDING - from CI VM to OpenVPN client (virbr0 --> tun0)
# ---------------------------------------------------
# allow any traffic for OpenVPN users:
-A FORWARD -i virbr0 -o tun0 -j ACCEPT
# FORWARDING - from OpenVPN client to CI VM (tun0 --> virbr0)
# ---------------------------------------------------
# allow any traffic for OpenVPN users
-A FORWARD -i tun0 -o virbr0 -j ACCEPT
# FORWARDING - from OpenVPN to Internet (tun0 --> eth0)
# -----------------------------------------------------
-A FORWARD -i tun0 -o eth0 -j ACCEPT
# FORWARDING - from kvm to kvm (virbr0 --> virbr0)
# ----------------------------------------------------
-A FORWARD -i virbr0 -o virbr0 -j ACCEPT
# FORWARDING - from Internet to OpenVPN clients (eth0 --> tun0)
# -------------------------------------------------------------
# FORWARDING - from Internet to CI VM (eth0 --> virbr0)
# ----------------------------------------------------
# FORWARDING - from CI VM to Internet (virbr0 --> eth0)
# ----------------------------------------------------
-A FORWARD -i virbr0 -o eth0 -j ACCEPT
# FORWARDING - from NTTNode to OpenVPN clients (eth2 --> tun0)
# ----------------------------------------------------
-A FORWARD -i eth2 -o tun0 -j ACCEPT
# COMMIT filtering rules
COMMIT
#################################################################################
# NAT table:
#################################################################################
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
# enable NAT for any outgoing traffic (eth2-->eth0 or tun0-->eth0)
-A POSTROUTING -o eth0 -j MASQUERADE
# COMMIT NAT rules
COMMIT
Subscribe to:
Comments (Atom)